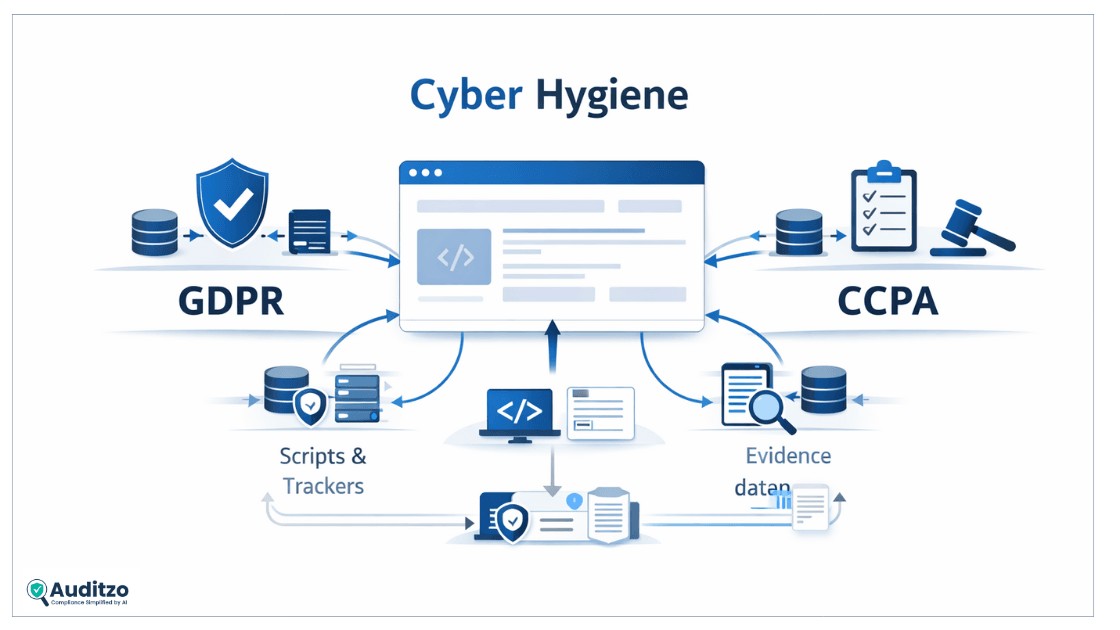
What Cyber Hygiene Really Means in Modern Compliance
Cyber hygiene is often misunderstood because it sits at the intersection of technology and law.
From a legal-tech compliance perspective, cyber hygiene is the baseline operational discipline your website or digital product follows when handling user data. It covers how data is collected, where it flows, who receives it, and whether those actions are intentional, documented, and lawful.
- It is not the same as cybersecurity.
- It is not the same as penetration testing.
- And it is definitely not limited to “we didn’t get hacked.”
A helpful way to think about cyber hygiene is basic sanitation in a commercial kitchen. A restaurant doesn’t wait for customers to get sick before cleaning surfaces. Regulators expect the same mindset: ongoing cleanliness, not crisis response. Compliance works the same way.
Cyber hygiene vs traditional security thinking
Most organizations still approach risk in silos.
- Security teams focus on breaches, malware, and exploits
- Legal teams focus on policies, consent language, and contracts
- Marketing teams deploy tools, trackers, and scripts freely
Cyber hygiene is what connects these silos into a single operational reality.
It answers the questions regulators and lawyers actually ask when reviewing a website:
- Do you know what scripts run on your website?
- Do you know what data they transmit?
- Do you know who receives that data and on what legal basis?
- Can you prove this at a specific point in time?
Under GDPR, CCPA, and especially CIPA, ignorance is not a defense. If your website loads third-party code that transmits user data, courts increasingly assume intent unless you can show otherwise.
Why the definition changed after 2023
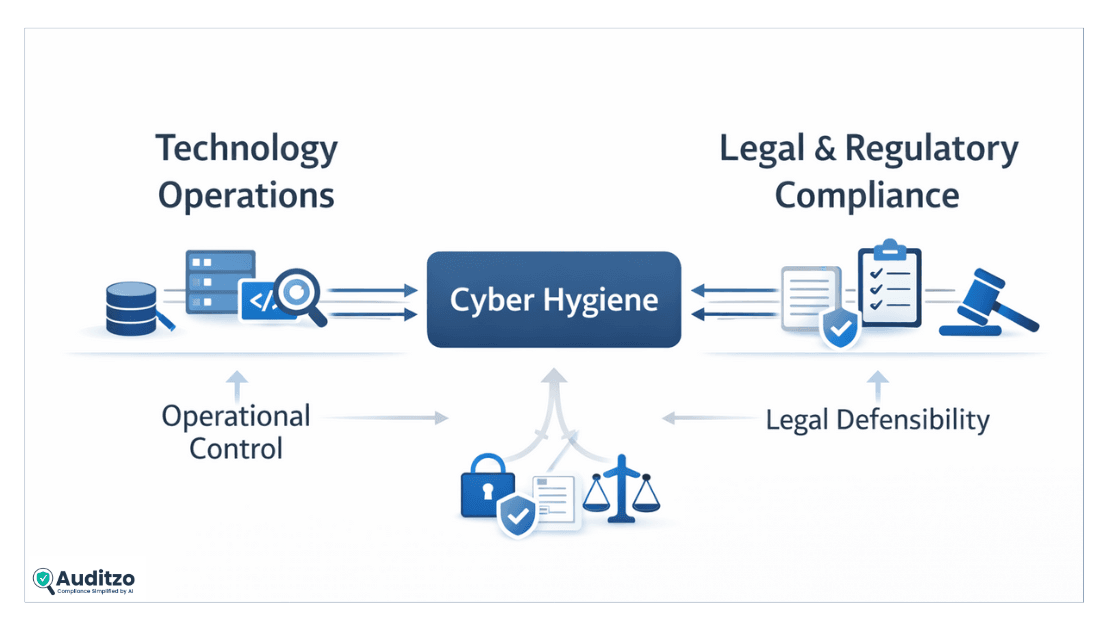
For years, cyber hygiene was treated as an internal IT concern. After 2023, it became a regulatory and evidentiary concept.
Three shifts drove this change:
- Increased enforcement around cookies, trackers, and consent
- Broader interpretations of wiretapping and interception, particularly under CIPA
- Courts accepting technical artifacts like HAR files, network logs, and screenshots as admissible evidence
As a result, cyber hygiene now means operational control plus legal defensibility — not just technical neatness.
Why Poor Cyber Hygiene Creates Legal Risk Under GDPR, CCPA & CIPA
Most compliance failures don’t begin with a breach. They begin with neglect.
Poor cyber hygiene creates legal exposure in ways that are subtle, cumulative, and easy to miss — until a regulator, plaintiff’s attorney, or forensic expert examines how your website actually behaves.
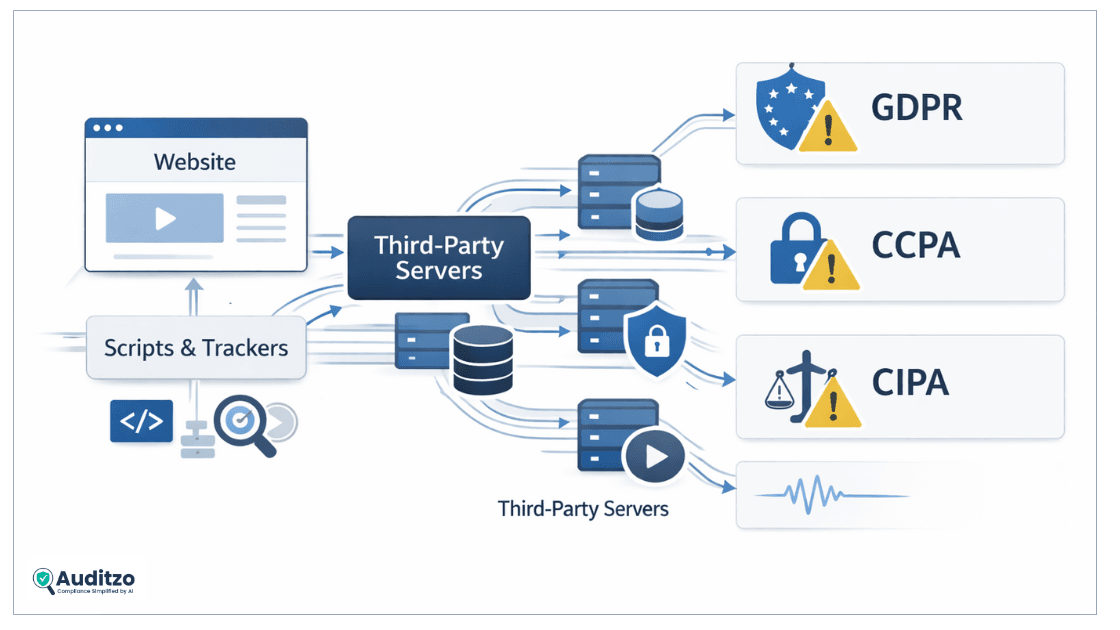
GDPR: “Reasonable security” is operational, not theoretical
GDPR does not require perfect security. It requires appropriate technical and organizational measures.
Poor cyber hygiene signals the opposite:
- Trackers firing before consent
- Scripts loading from unknown or undocumented domains
- Data transmitted without a clear, documented purpose
- Inconsistent behavior across regions or devices
When regulators assess GDPR compliance, they look for patterns. Cookie-related violations are often documented through structured technical evidence rather than policy language alone, as shown in many GDPR evidence reports for cookie violations.
Regulatory expectations around these controls are further clarified in EDPB guidance on technical and organizational measures under GDPR, which emphasizes demonstrable control over data processing.
Disorganized data flows and undocumented third-party behavior point to systemic non-compliance, even when no data breach has occurred.
CCPA / CPRA: “Sharing” happens at the network level
Under CCPA, many organizations still assume “sharing” means intentionally selling data.
In practice, cyber hygiene failures create unintentional sharing:
- Analytics and advertising scripts transmitting identifiers
- Session replay tools capturing user interactions
- Consent misconfigurations causing silent data leakage
From a legal standpoint, intent matters less than outcome. What matters is whether sharing occurred — and whether you can show control. This interpretation is reinforced by California regulatory guidance on data sharing under CCPA and CPRA, which focuses on real data flows rather than stated intentions.
CIPA: where cyber hygiene becomes litigation fuel
CIPA is where cyber hygiene failures become especially risky.
Plaintiffs don’t need proof of a breach. They need evidence that:
- Communications were intercepted
- Third parties received data
- The user did not consent
Poor cyber hygiene makes this easy to demonstrate. Network requests, script behavior, and cookie synchronization patterns quickly become exhibits in lawsuits.
These issues are examined in depth in legal analysis of digital interception under wiretapping laws, which explains how courts assess interception in modern digital contexts.
That’s why many CIPA cases start with a simple question:
“Why was this third-party script present at all?”
The Cyber Hygiene Checklist Regulators and Lawyers Expect
This is the core of the playbook.
Regulators and litigation teams don’t evaluate cyber hygiene in the abstract. They look for specific, observable controls that can be independently verified.
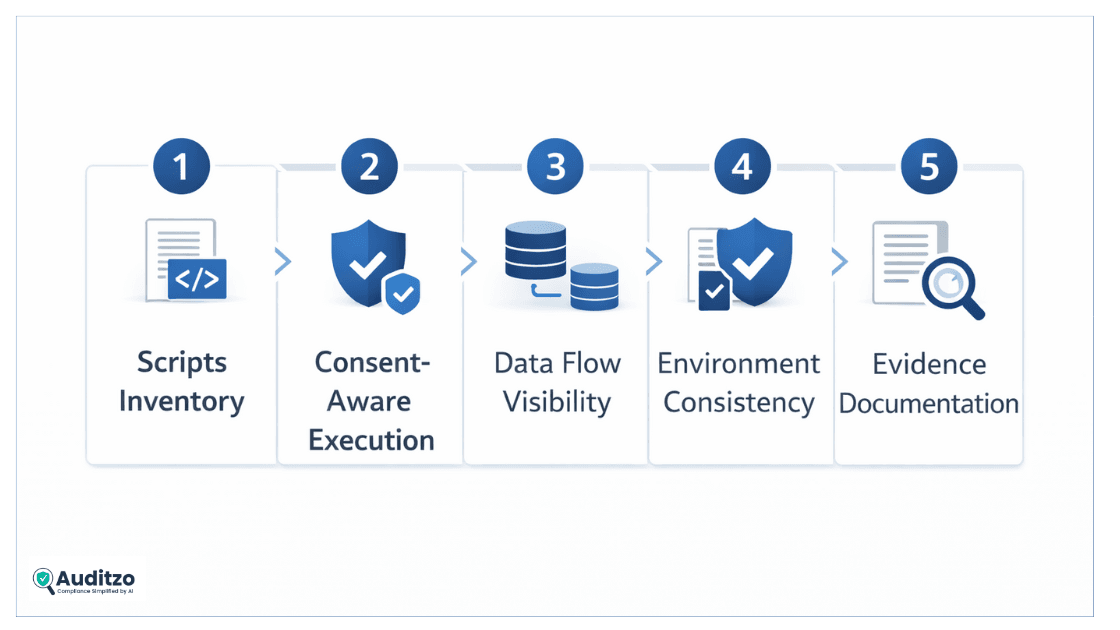
1. Script and tracker inventory control
You should be able to answer, without hesitation:
- What scripts load on each page
- Who owns them
- What data they access or transmit
If your answer relies on assumptions (“it’s just Google Analytics”), that’s a hygiene failure.
Good hygiene means maintaining an inventory tied to business purpose and consent category.
2. Consent-aware execution logic
Cyber hygiene requires scripts to behave differently before and after consent.
This is not a banner problem — it’s an execution problem.
Regulators look closely at:
- Whether network requests fire before consent
- Whether fallback scripts still transmit data
- Whether regional logic actually works as intended
A consent banner that looks compliant but fails technically is worse than no banner at all.
3. Third-party data flow visibility
Most legal risk exists outside your own servers.
Cyber hygiene requires:
- Visibility into outbound requests
- Understanding of cookie syncing
- Awareness of cross-domain data transfers
Lawyers often uncover violations by mapping these flows visually. If you can’t map them yourself, you’re already at a disadvantage.
4. Environment and configuration consistency
Many violations occur only in specific contexts:
- Certain geographies
- Mobile devices
- Logged-in user states
- Edge-case journeys
Good hygiene means testing real-world behavior, not just ideal scenarios in staging environments.
5. Evidence-ready documentation
This is where cyber hygiene turns into legal strategy.
Regulators and courts expect:
- Time-stamped evidence
- Reproducible observations
- Clear linkage between behavior and legal interpretation
If you can’t demonstrate what your website did on a specific date, defending it later becomes extremely difficult.
Cyber Hygiene vs Security Audits vs Compliance Audits
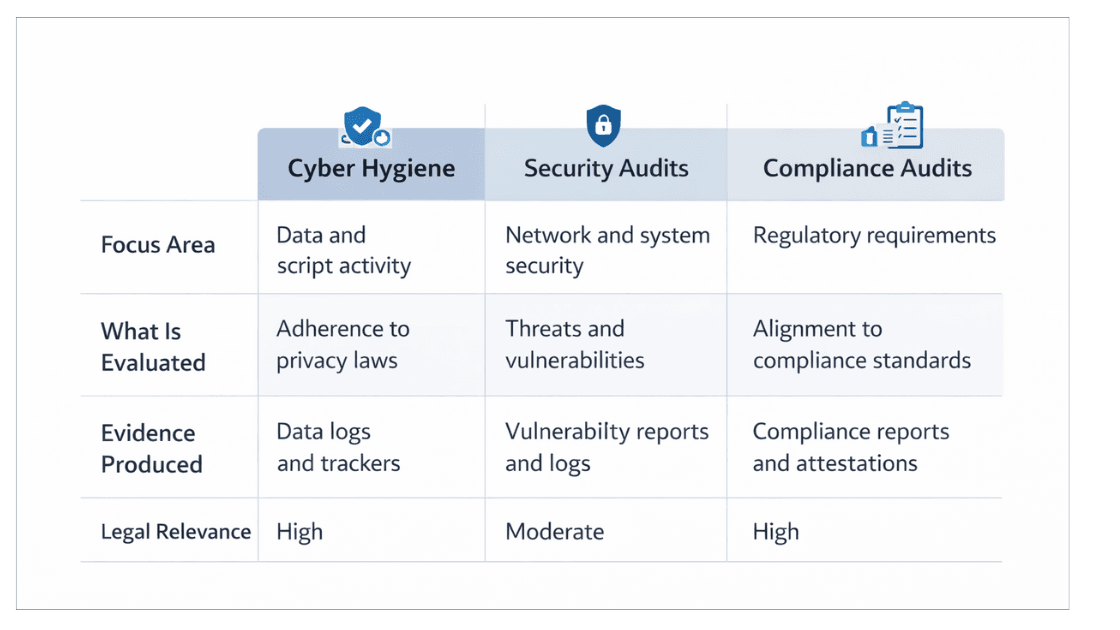
This distinction causes constant confusion, and often leads to misplaced confidence.
Security audits: breach-focused
Security audits answer questions like:
- Can someone break in?
- Are there vulnerabilities?
- Is infrastructure hardened?
They are essential, but they do not assess legal exposure arising from normal website operations.
Compliance audits: policy-focused
Traditional compliance audits concentrate on:
- Privacy policies
- Consent language
- Data processing agreements
They often stop at documentation and never validate what actually happens in the browser.
Cyber hygiene audits: behavior-focused
Cyber hygiene audits examine:
- What actually happens in the browser
- What data flows occur by default
- Whether behavior matches policy and consent
This is why cyber hygiene has become the missing link between IT, compliance, and legal teams.
A clean security audit does not protect you from CIPA.
A well-written privacy policy does not stop unauthorized interception.
Only disciplined cyber hygiene does.
How Cyber Hygiene Evidence Is Used in Investigations and Lawsuits
This section matters most to lawyers and decision-makers.
In modern enforcement and litigation, technical behavior becomes narrative.
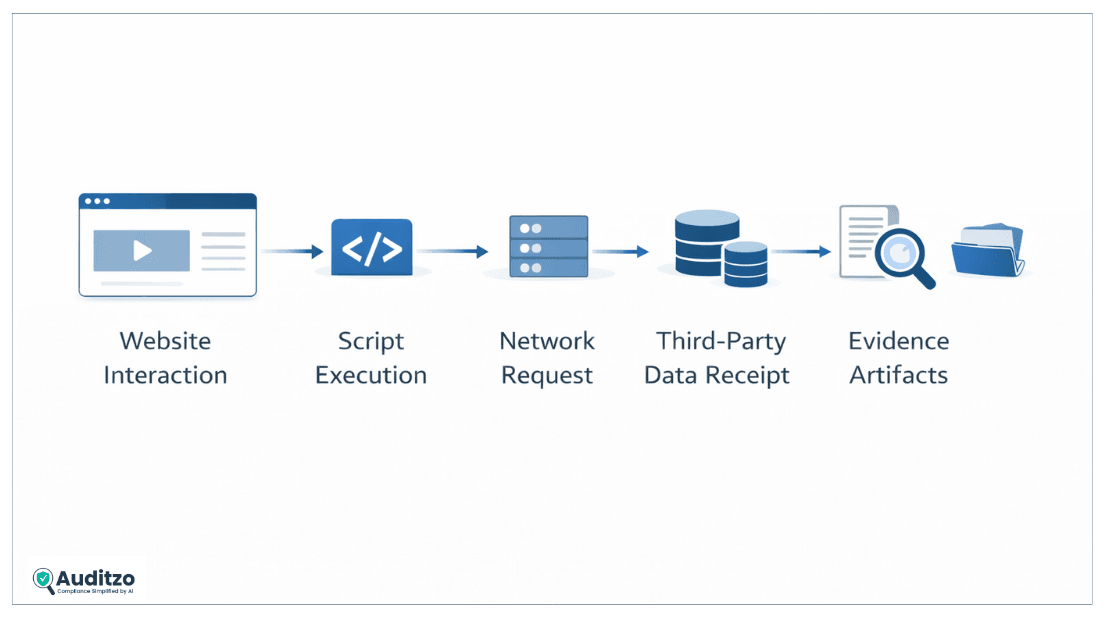
From network request to legal argument
A typical progression looks like this:
- A script loads on page visit
- A network request transmits identifiers
- A third party receives data
- Consent is missing or invalid
Each step can be captured, timestamped, and presented as evidence.
Courts increasingly accept technical artifacts as valid digital evidence when assessing whether unauthorized data interception or sharing occurred, including what qualifies as valid digital evidence under GDPR and CIPA.
These steps can be documented using screenshots, logs, and HAR files as courtroom evidence — artifacts whose technical legitimacy is grounded in standard browser behavior described in browser network request and storage behavior documentation.
This is why cyber hygiene is no longer theoretical. It either produces defensible artifacts — or exposes the lack of them.
Why “we didn’t know” fails in court
Poor hygiene signals negligence.
When organizations cannot explain:
- Why a script existed
- Who approved it
- What data it accessed
Courts infer a lack of reasonable control. Under statutes like CIPA, intent can be inferred directly from this conduct.
Operationalizing Cyber Hygiene With Continuous Monitoring
Cyber hygiene is not a one-time checklist. Websites change constantly.
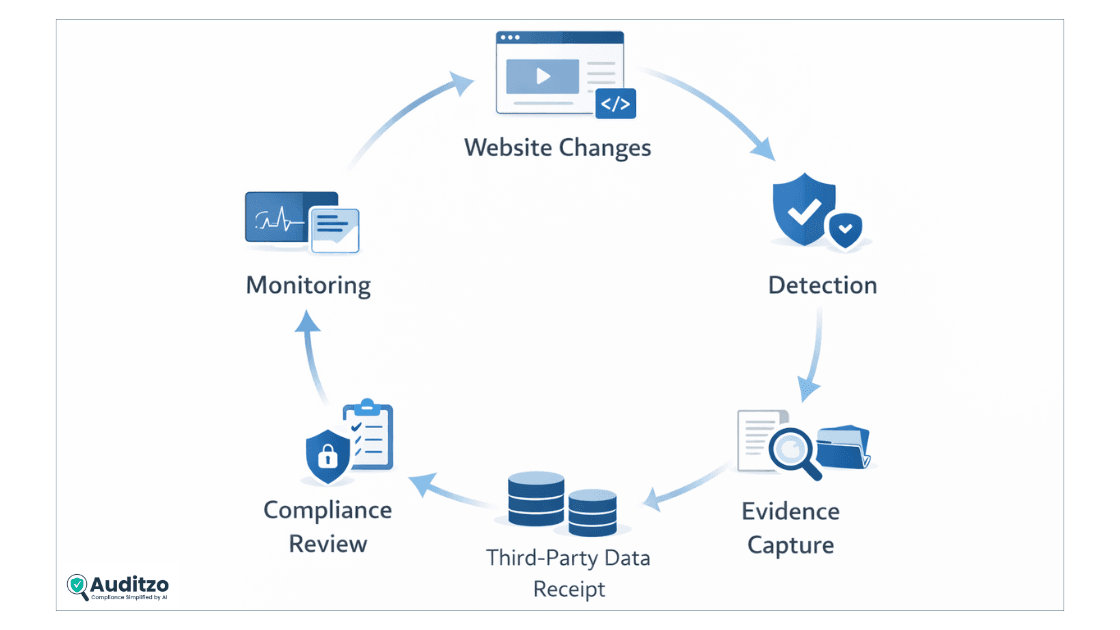
New marketing tools, A/B tests, tag manager updates, and CMS plugins quietly introduce risk. A site that was compliant last quarter can drift into violation without anyone noticing.
Why point-in-time audits fail
Point-in-time audits answer one question:
“What happened on this day?”
Regulators and courts ask a more important one:
“What usually happens?”
Continuous cyber hygiene monitoring focuses on:
- Detecting new scripts and trackers
- Identifying behavioral changes
- Preserving historical evidence
This shift is especially important for organizations operating across multiple sites and jurisdictions, as shown in a multi-site GDPR and CIPA compliance audit.
From hygiene to defensibility
Organizations with strong cyber hygiene can:
- Demonstrate intent to comply
- Show rapid remediation
- Provide structured evidence
This doesn’t eliminate risk — but it significantly reduces exposure and strengthens legal position.
Conclusion: Cyber Hygiene Is the New Compliance Baseline
In 2026, cyber hygiene is no longer optional, theoretical, or purely technical.
It is the operational proof that:
- You understand your data flows
- You control third-party behavior
- You respect user consent
- You can defend your practices under scrutiny
For most organizations, the next step is not rewriting policies, but validating how the website actually behaves in real user sessions. Reviewing evidence, comparing observed behavior against legal expectations, and understanding where gaps exist is what turns awareness into defensibility.
GDPR, CCPA, and CIPA enforcement increasingly target how websites behave, not just what they promise. Cyber hygiene is how those promises become real.
FAQs
What is cyber hygiene in compliance terms?
Cyber hygiene refers to the operational discipline a website follows to control scripts, trackers, data flows, and consent behavior in a legally defensible way.
Is cyber hygiene legally required?
While not named explicitly in statutes, regulators and courts treat cyber hygiene as part of “reasonable security” and lawful data processing under GDPR, CCPA, and CIPA.
How is cyber hygiene different from cybersecurity?
Cybersecurity focuses on preventing attacks. Cyber hygiene focuses on controlling normal data behavior that creates legal exposure even without a breach.